“It will never happen to me.”
Yup, that quote above is something I said to myself every time I was warned of using the same password twice or thrice. I managed around 10-20 different passwords for all of my accounts. Some were easy (and I knew it), others were more difficult and I had around 2-3 very long passwords for those critical apps (like PayPal). I thought I was safe. I read similar posts to what you’ll be reading and all I had in mind was: “It will never happen to me. My passwords are long and difficult.”
But then this happened:
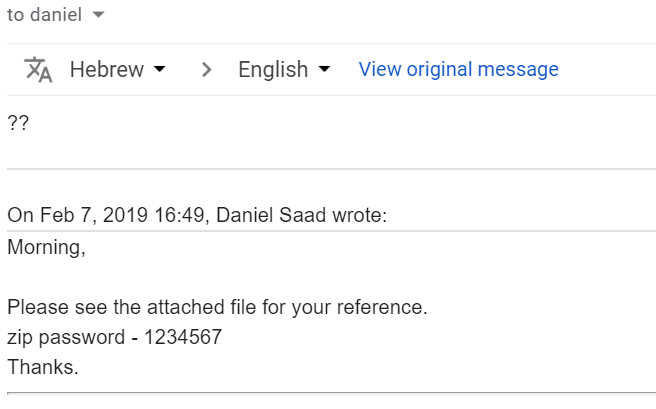
A friend whom I haven’t talked to in months sends me a message asking what is the email all about. I asked myself the same.
Some dubious attachment was added to the email with a password sent from MY account.
It wasn’t me, I swear!
I wasn’t completely satisfied with the anti-virus’ warnings, so I safely investigated it myself. It was a word document in an old format with macros trying to run.
I logged in to that account (most of my domain email addresses are forwarded to my gmail), and realized that since September 2018 I have been receiving Sextortion emails.
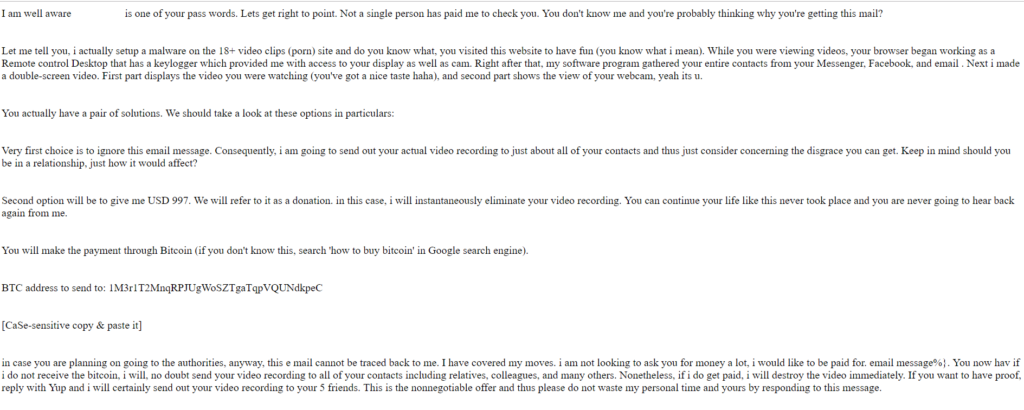
Boom! Another one:
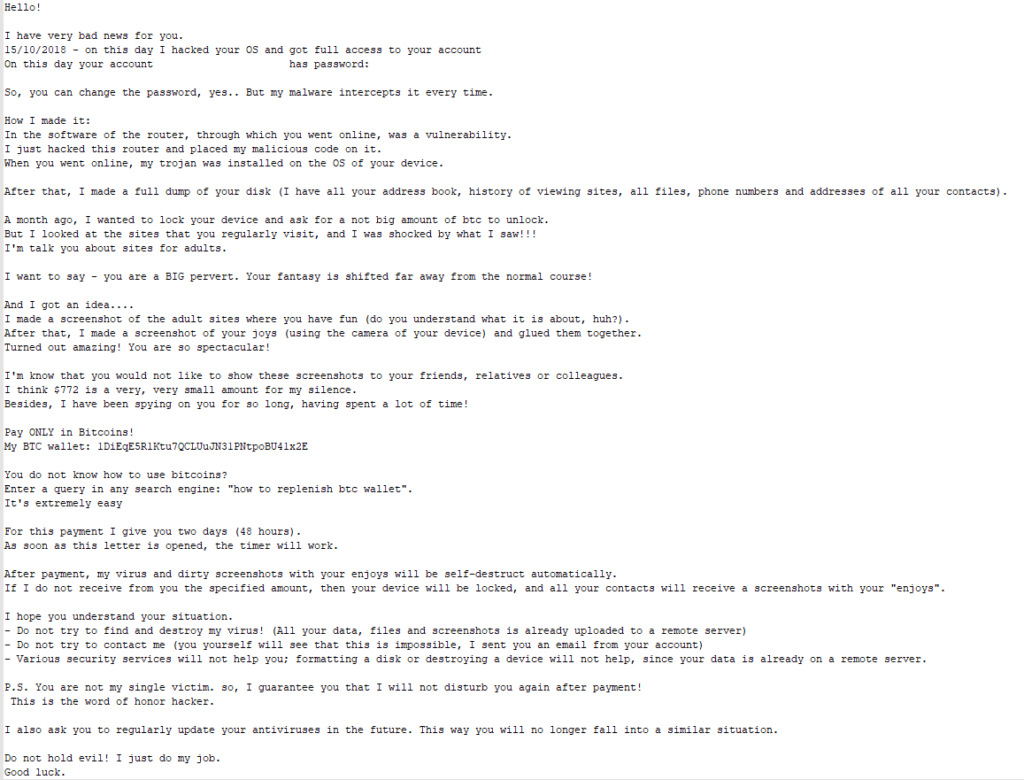
And you thought there were only two?
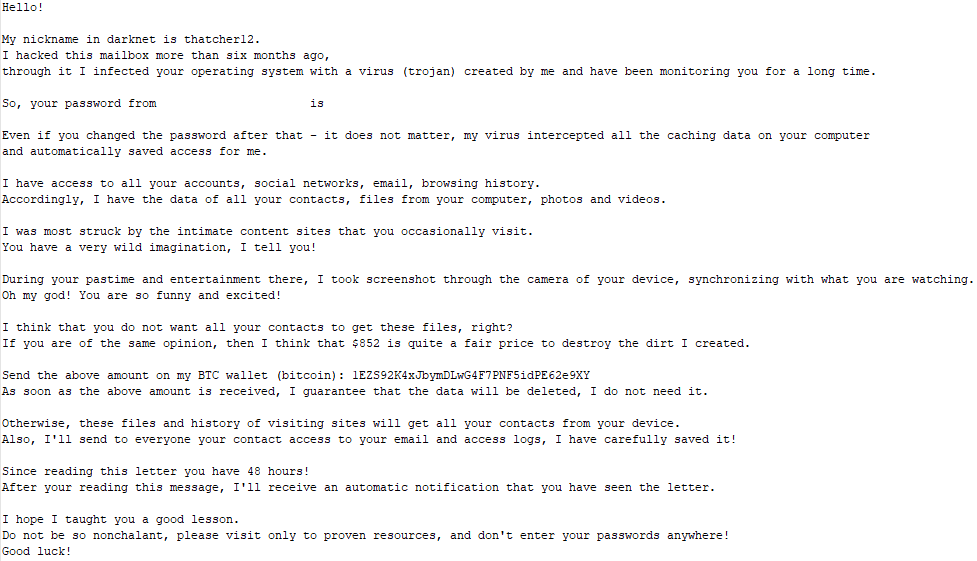
I can probably put together a whole book out of these emails. The above 3 are nothing compared to the plethora of ransom emails I was receiving.
To be honest, there are so many holes and blisters in those emails that it just made me giggle. The FBI published a service announcement last year about this scam. You can also Google “sexploitation ransomware emails”, or enjoy a gloomy yet related episode of Black Mirror: Shut Up and Dance. But… Let’s get back to where we just were!
A bunch of script kiddies got a hold of my very old passwords, entered my old email account and started emailing people I’m in contact with viruses in disguise as “proof”.
At this point I was just too curious to know HOW?!
I remembered an old lecture about security on the net. We were introduced to http://haveibeenpwned.com which tells you whether your credentials participated in any mass credential breaches.
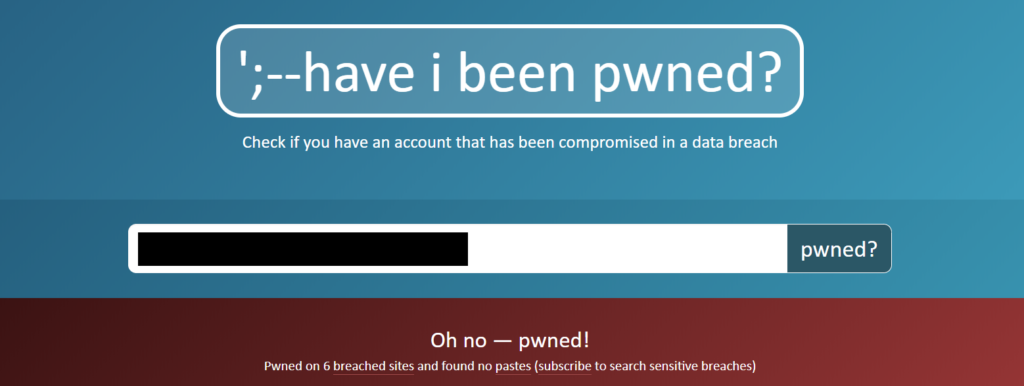
I have been feeling lucky! I managed to register to not 1, not 5, but 6 irresponsible websites which apparently didn’t save my password correctly. Alright, maybe I’m blaming them more than they deserve and my bad habit of re-using the same password should also be blamed. But REALLY? My account for all I know could have had every hacker on the dark net login to it, send some shady email and leave.
So what now? I have registered to a TON of websites in the past few years. I myself barely remember which passwords were used where.
Hey! Wait a minute. I work for CyberArk! CyberArk solves this problem for enterprises. What’s out there for people like you and me who simply want to stay safe?
Password Managers. A password manager is a tool that saves your account passwords and when you login it fills it in automatically. Browsers like chrome have a simple password management implementation. Today’s password managers can do a lot more!
First, they retrieve all of your saved passwords from your browser. Then they allow you to rotate and generate new (stronger) passwords for all of your accounts at a push of a button. When you login to one of your accounts, they will fill the generated password automatically. When you use a password manager, your real passwords will not be exposed in account breaches and pastes.
There were 3 password manager alternatives I’ve looked in:
All three made a good impression on me. I decided to just try them out one by one until I’m satisfied. I started with dashlane thanks to this guide but to be honest, all three had amazing reviews. I had to start somewhere before my colleagues block me for sending them spam and cheap viruses.
Set up was quick and easy. It automatically recognized around 160 services right off of my chrome browser and clearly made me face my bad habit. As you could have guessed, I wasn’t too creative when registering to these 160 services. I had to re-use at least one password… Lets put it right on the table: I had ten to twenty circulated passwords waiting for the next breach.
Since these solutions are very new to me hands-on I’ll only be able to compare them after more experience authenticating on the net. Tune in and I may compare them myself in the future. For now you’ll have to settle for other (awesome) blogger’s comparisons.
Now that I look back I’m feeling a bit silly for thinking I was safe. No one is safe.
Don’t wait for the next breach. It will happen sooner or later. ACT TODAY.
Also published on Medium.



3 Responses
You are the best!!!
It’s a pity you don’t have a donate button! I’d most certainly donate to this excellent blog! I guess for now i’ll settle for book-marking and adding your RSS feed to my Google account. I look forward to fresh updates and will share this blog with my Facebook group. Chat soon!
Extremely informative….looking forward to visiting again.